Automate SentinelOne Incident Alerts to Microsoft Teams with Power Automate
In today’s fast-paced cybersecurity landscape, rapid response to threats is critical. SentinelOne offers powerful endpoint protection with real-time threat detection, but ensuring that your team is immediately aware of new incidents can be a challenge—especially if alerts are buried in dashboards or emails. By integrating SentinelOne with Microsoft Teams, you can streamline your incident response workflow and ensure that critical alerts are delivered directly to the channels where your team collaborates most.
In this guide, I’ll show you how to automatically post new SentinelOne incidents to Microsoft Teams using a combination of SentinelOne APIs, Microsoft Power Automate, and optionally, Adaptive Cards. Whether you’re a security analyst or an IT administrator, this integration will help you stay ahead of threats and respond faster—right from within Teams.
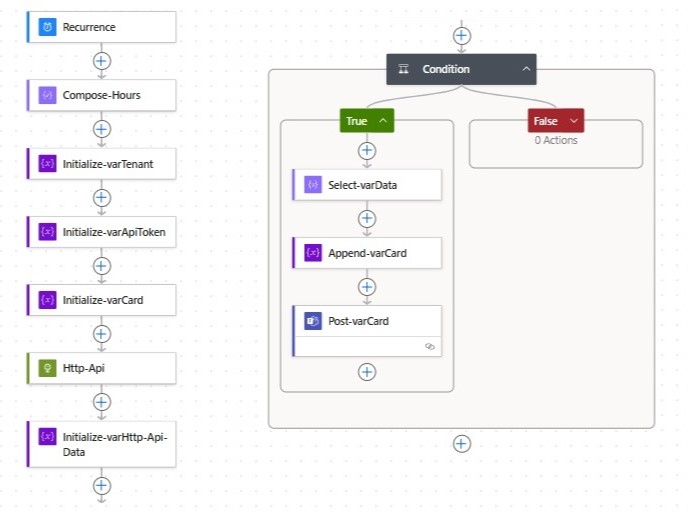
What You’ll Need
- A SentinelOne account with API access
- Access to Microsoft Teams workspace and a channel (or a chat group)
- Access to Microsoft Power Automate
Step-by-Step Integration Guide
1. Generate SentinelOne API Token
Start by getting your SentinelOne API token from the console. You’ll need this to authenticate API requests from Power Automate.
2. Create a New Power Automate Flow
Go to https://flow.microsoft.com. Create a new Automated cloud flow or Instant cloud flow.
3. Give it a name and click Skip to configure manually
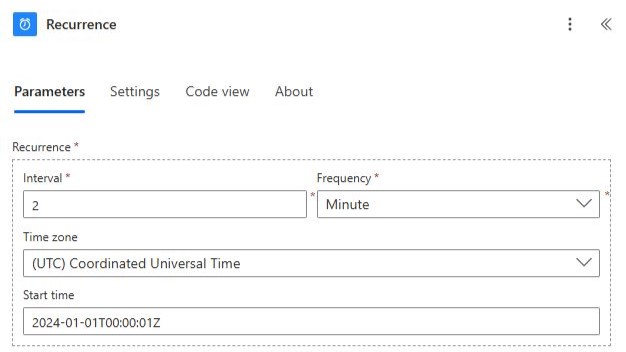
4. Add a Recurrence Trigger (Polling Schedule)
Add a (Schedule) Recurrence trigger with these details:
| Field | Value |
| Interval | 2 |
| Frequency | Minute |
| Time zone | (UTC) Coordinated Universal Time |
| Start time | 2024-01-01T00:00:01Z |
This step defines how frequently Power Automate will check SentinelOne for new incidents.
5. Create a Timestamp for Filtering
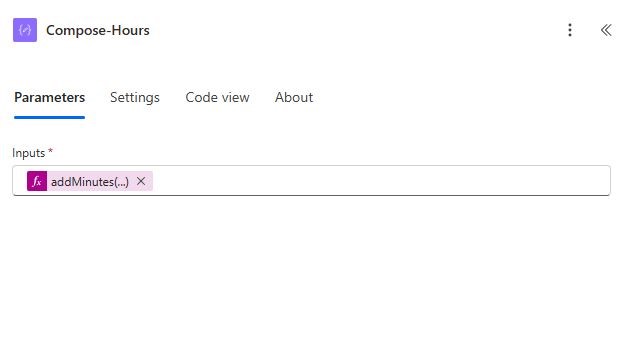
Add a (Data Operation) Compose action. Rename the action to Compose-Hours. On the Inputs field, insert an expression. Add the text below as a String function.
| Inputs |
| @addMinutes(utcNow(),-2) |
To avoid re-processing old data, you’ll compute a timestamp for “2 minutes ago”—which helps filter new incidents only.
6. Initialize Global Variables
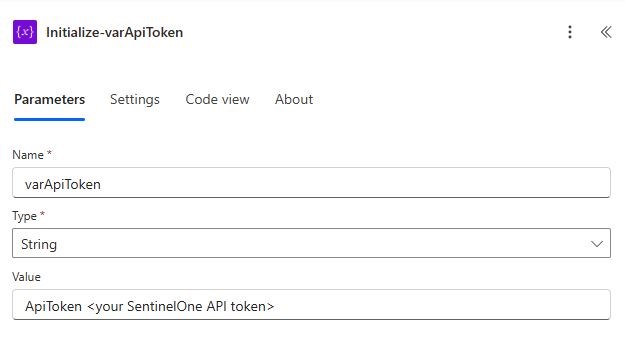
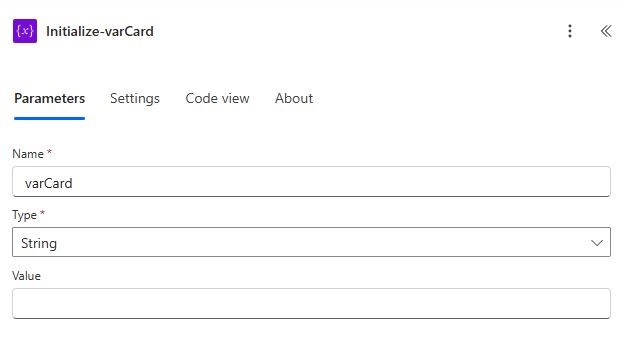
Add a (Variable) Initialize variable action. Do this for each of the mentioned variables below:
| Action Name | Name | Type | Value |
| Initialize-varTenant | varTenant | String | https://<your SentinelOne tenant URL> |
| Initialize-varApiToken | varApiToken | String | ApiToken <your SentinelOne API token> |
| Initialize-varCard | varCard | String | <empty> |
You’ll need a few variables to make things clean and reusable. These will be used in the HTTP request and Adaptive Card message later.

7. Call SentinelOne API for New Threats
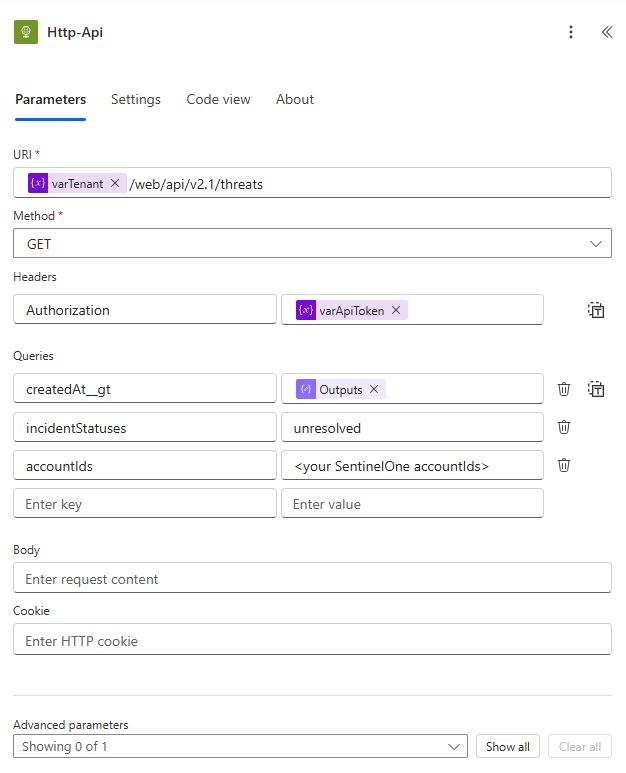
Add a (HTTP) HTTP action. Rename the action to Http-Api. Use the details below:
| Field | Sub-field | Value |
| URI | @{variables(‘varTenant’)}/web/api/v2.1/threats | |
| Method | GET | |
| Headers | Authorization | @{variables(‘varApiToken’)} |
| Queries | createdAt__gt | @{outputs(‘Compose-Hours’)} |
| incidentStatuses | unresolved | |
| accountIds | <your SentinelOne accountIds> |
This fetches only unresolved incidents created in the past 2 minutes.
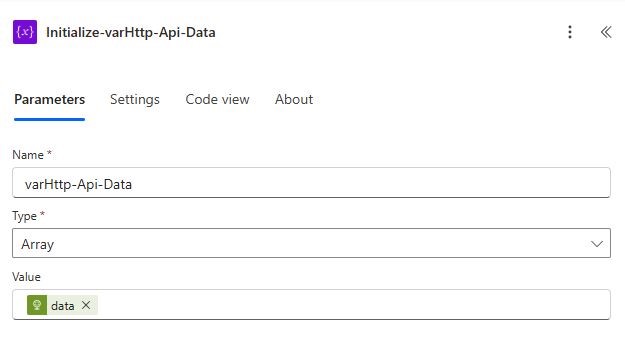
8. Parse the API Response
You’ll need to extract the .data array from the response, which contains all the relevant incidents. Add a (Variable) Initialize variable action wth the following details:
| Action Name | Name | Type | Value |
| Initialize-varHttp-Api-Data | varHttp-Api-Data | Array | @body(‘Http-Api’).data |
This makes it easier to loop through or format the incidents later.
9. Check if There Are New Incidents
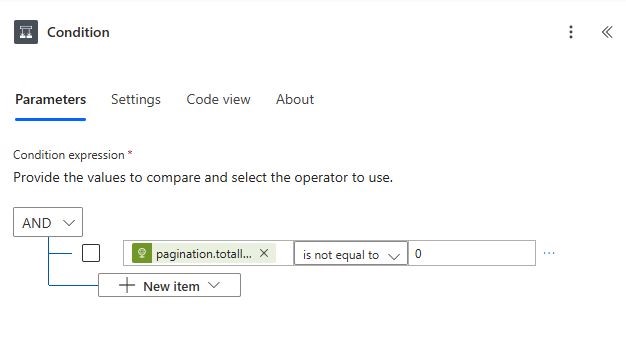
Add a (Control) Condition action. Add below details as the Condition expression.
| Choose a value | Operator | Choose a value |
| @body(‘Http-Api’).pagination.totalItems | is not equal to | 0 |
If this returns true, the workflow proceeds to build the message.
10. Perform all the following steps when the Condition is true.
10.1. Let’s create individual message blocks for each incident found.
Add a (Data Operation) Select action. Add the details below:
| Field | Sub-field | Value |
| From | @variables(‘varData’) | |
| Map | type | TextBlock |
| text | ▸ [@{item().id}](@{variables(‘varTenant’)}/incidents/threats/@{item().id}/overview) | AI Confidence Level: @{item().threatInfo.confidenceLevel} | Threat Status: @{item().threatInfo.mitigationStatus} | |
| wrap | true | |
| spacing | None |
This turns each incident into a clickable, readable message format.
10.2. Build the Adaptive Card
Add a (Variable) Append to string variable action. Choose the varCard variable as value on the Name field and add the following as Value:
{
"type": "AdaptiveCard",
"$schema": "http://adaptivecards.io/schemas/adaptive-card.json",
"version": "1.4",
"msteams": {
"width": "Full"
},
"body": [
{
"type": "TextBlock",
"text": "SentinelOne • New Alert",
"wrap": true,
"size": "Large",
"color": "Attention",
"weight": "Bolder"
},
{
"type": "TextBlock",
"text": " @{convertFromUtc(utcNow(), 'GMT Standard Time', 'ddMMMyyyy HHmm')}(UTC)",
"wrap": true,
"style": "heading",
"size": "Small",
"spacing": "None",
"isSubtle": true
},
{
"type": "TextBlock",
"text": "New and active incident(s)",
"wrap": true,
"size": "Small",
"isSubtle": true,
"horizontalAlignment": "Right"
},
{
"type": "ColumnSet",
"separator": true,
"spacing": "Medium",
"columns": [
{
"type": "Column",
"width": "stretch",
"items": @{body('Select-varData')}
}
]
}
]
}This card shows a title, timestamp, and incident summaries dynamically.
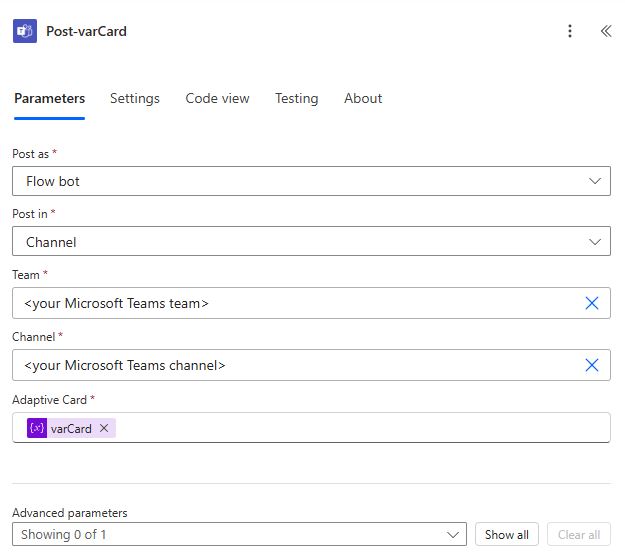
10.3. Post the Card to Teams Channel
The final step is to post the Adaptive Card to your designated Microsoft Teams channel.
Add a (Microsoft Teams) Post card in a chat or channel action. Add the details below:
| Parameter | Value |
| Post as | Flow bot |
| Post in | Channel |
| Team | <your Microsoft Teams team> |
| Channel | <your Microsoft Teams channel> |
| Adaptive Card | @variables(‘varCard’) |
Boom. Your team is now getting real-time alerts, nicely formatted, right inside Teams.

With this integration, new SentinelOne incidents show up in Teams within minutes of being detected. Analysts can click the links directly to jump into SentinelOne and take action fast. No more toggling tabs, no more missed threats.